“An IT system is as secure as its weakest component.”
We all know that ensuring the security of our IT infrastructure is critical for end-user satisfaction, smooth applications and business success. But are we aware of what we can rely on from our IT service provider and what actions we should take on our side?
Security is a joint effort between customers, developers, sysadmins, and service providers (infrastructure, network, etc). No matter how experienced in IT security your infrastructure provider is, there are certain actions each business should take on its own to ensure it is secure. You might be using the best technology on top of your servers or application, but if there is a vulnerability within the application, there is no technology that would be able to protect it. Achieving the ultimate level of online security can be done only by combining the knowledge and expertise of a managed IT services provider and your own responsibility.
In this article CloudScale 365 security experts are providing an overview of how we ensure your security together with a practical guide on what actions you need to take on your own to protect your applications and workloads online.
As a managed service provider, we ensure a secure environment covered by different layers including but not limited to Physical Security, Network Security and Personnel Security. Here you will find a description of each of the security components and their scope. In addition, we believe that our customer’s responsibility and proactiveness is also vital factor in achieving the ultimate layer of security.
According to a recent Gartner report, through 2025, a full 99% of all cloud security failures will result from user error. The good news is that these issues can be prevented in virtually all cases when the IT infrastructure users understand their roles and responsibilities in cloud security.
While CloudScale 365 cares for the infrastructure and its maintenance in operational conditions, our customers are entirely responsible for the way their applications are built, updated and maintained. In certain specific cases, we are happy to support our customers in their efforts to ensure their online security, by providing our Ops as a Service solution. Under all circumstances, you are responsible for properly configuring and using the services we provide and taking your own steps to maintain appropriate security, protection, backup, etc.
Customer Responsibility
As a service provider, we are responsible for the security of the cloud, while as a customer you are responsible for security in the cloud. Our customers are responsible for securing their servers, users, services, and applications such as SSH, SFTP, FTP, SMTP, HTTP, HTTPS, Java, etc. We put our best efforts to provide the highest level of security for our data centers and networking, but all security within the server is customer’s responsibility. Servers come with a default set of rules and fail2ban pre-installed, however, customers need to configure the tools according to their needs to ensure they are protected. CloudScale365 cannot take responsibility for unsecured services running on customers’ servers.
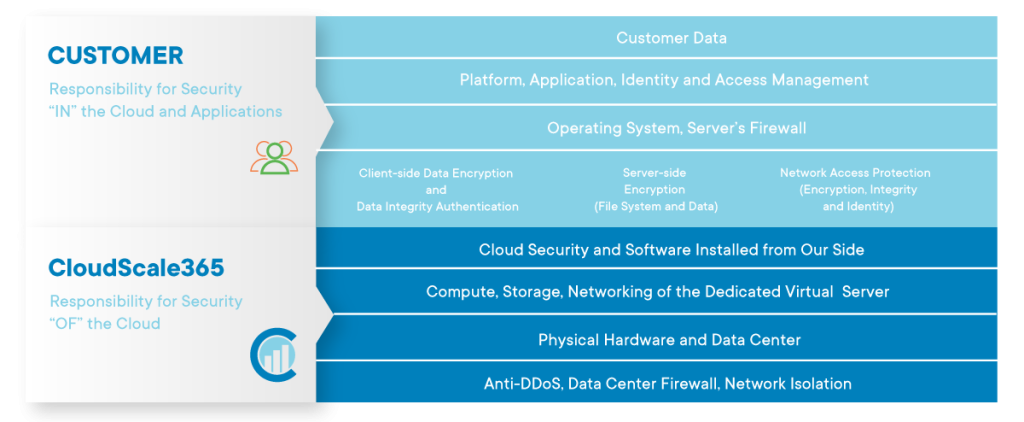
All Levels on Which CloudScale365 Hosting Division Ensures Your Security
DATA CENTER RESOURCES
Your Data Center resources are provided and hosted by Quality Technology Services. This is one of the largest data center operators in the USA. QTS complies with the highest standards of operation. All QTS data centers are SOC1 and SOC2 certified. QTS has designed a comprehensive security program that unifies physical and cyber security under a centralized security umbrella to achieve a more holistic view of the risk landscape. We can provide QTS compliance reports for industry standards.
PHYSICAL SECURITY
We currently lease space and facilities in the Suwanee, GA and Richmond, VA data centers. Only a few designated personnel within our organization have site access. They must have a photo ID entry key which provides access to the facility lobby only. They must then check in with a 24/7 manned security desk to have their entry key activated for data center floor access. There are multiple separate biometric access control activated doors (two fingerprint stations and one retina station) to pass onto the data center floor. The physically separate doors are monitored with surveillance cameras by security personnel and are designed to prevent tailgating. Our operation is housed in a locked cage on the data center floor. Our personnel must check in at the floor operations office inside the data center to obtain a key to our cage. The floor operations office has real-time access to their security system telling them who is on the floor and where they are at all times. Keys must be checked out and checked in each time the cage needs to be entered. When our personnel exit the facility their entry key is then deactivated for data center floor access. Here is a link to their site that provides a lot of information and a virtual tour of the data center.
More information about the data center physical security and the unique converged security approach of QTS you can find here: http://www.qualitytech.com
NETWORK SECURITY
While there is no network immune from attacks, a stable and efficient network security system is essential to protect data and ensure business continuity. At CloudScale365 we employ a number of mechanisms to guarantee network security.
1. Fortinet Firewall – In our QTS data centers we have an industrial-strength Fortinet firewall that has rules set up to restrict access to certain ports as well as to detect and stop denial of service attacks. Fortinet is a major network equipment and services provider, landing high in the Gardner magic quadrant.
2. VPN – all of our internal and administrative systems can only be accessed through a Virtual Private Network (VPN) that is for the exclusive use of our employees. The access list is controlled by our LDAP-based directory service which allows us to immediately restrict access in the event that a person’s employment with eApps is terminated. Our staff must have a personal security certificate to access devices on the network. Also, we provide private VPN services for customers as an option. Our Private Cloud service includes a VPN gateway for administrative and back-end server access.
3. Password Control – All internal systems have a rigid password management process that ensures that passwords are secure and revised periodically. Also, our hosting management system requires that all customer-created passwords pass a cracklib test. This helps us enforce the usage of secure passwords. We also have a password scanner utility that we use on an as-needed basis when we suspect that a customer has a weak password.
4. 24/7/365 Monitoring – we use a sophisticated monitoring system that alerts us for not only outages but unusual levels of resource usage, with particular sensitivity to data transfer rates. This allows us to act quickly if our bandwidth usage spikes. Our data center operator also has a monitoring set up to detect unusual activity on our Internet circuit as well as power and temperature monitoring variances. We also provide resource monitoring and uptime monitoring for all customers at no additional charge.
5. Intrusion Detection/Prevention System (IDS) – Our firewall has a built-in intrusion detection system that alerts us and deactivates access protocols (such as SSH and FTP) whenever numerous attempts are being made to attempt to compromise an access protocol. The IDS also provides reports of abnormal activity.
6. Vulnerability and Malware Scanning – we perform various scans to identify vulnerabilities and malware that find their way onto our customer’s systems. We also provide malware scanning services to customers as an option.
7. Exploit/Vulnerability Response Process – we have an aggressive response policy regarding the identification of known exploits. We take appropriate action as soon as we determine that one of our customers has an exploit. In the case where a major exploit is reported to be in the wild, we form a response team. This team determines the impact within our network, assesses the risk, and implements an action plan to mitigate the risk. Our company received many compliments from customers for the way our response team handled the 2014 Heartbleed vulnerability.
8. DDoS Protection – CloudScale 365 employs multiple systems and processes to protect against both Inbound and Outbound DDoS attacks. These include automated Inbound DDoS protection systems provided by our Data Center providers. The inbound DDoS protection system is from Arbor Networks, a major vendor of DDoS protection systems.
We also have an option for enhanced DDoS/WAF protection through our partner StackPath. The use of this service is included free of charge for all eApps customers. This optional service works the same as CloudFlare’s $20 per month PRO plan and requires that the server is configured to hide (cloak) the assigned IP address, to prevent direct attacks against the IP.
SALES SECURITY
We have an extremely thorough order verification process for new customers. Since we implemented our order verification process in June of 2004 it is very rare for anyone to purchase our service using a stolen credit card. This effectively eliminates the possibility of a hacker posing as a legitimate customer to gain access to our services.
PERSONNEL SECURITY
We have a rigorous screening process for new hires. This includes extensive interviews and 5 types of background checks. New staff are trained on security policies and procedures as part of the onboarding process. Staff must sign a security and privacy agreement prior to beginning work.
We control access to our internal systems using a Virtual Private Network (VPN), LDAP-controlled access lists, and individual security keys instead of passwords on our servers. These tools allow us to block access by a former employee immediately in the event of they leaving the company, which is much faster than manually changing passwords on each server.
PRIVACY POLICY
We have a very strict privacy policy for all customers. We are GDPR compliant and adhere to the strict rules on privacy required by the European Union. We are also certified under the US Department of Commerce’s Privacy Shield program, which protects all EU citizens, and the corresponding program for Swiss citizens. We apply these policies to all customers worldwide. Here is a link to our Privacy Statement.
CREDIT CARD SECURITY
Most of our customers pay for their service using a credit card. Our payment processing systems use a credit card “vault” concept. What this means is that credit cards used by customers to pay for their eApps services are stored at the payment processor location and are processed using a token. This approach is recognized by the PCI compliance process as having a very high level of security. For our customers that process credit cards, we offer PCI compliance assistance services to help them achieve PCI compliance on their eApps servers.
CUSTOMER PCI COMPLIANCE
The CloudScale 365 hosting service is PCI-ready. However, PCI compliance is a shared responsibility between us and our customers.
1. Each customer’s application is unique and can have inherent PCI issues over which we have no control.
2. Customers have a responsibility to update their operating system components or migrate to a newer operating system when needed. We apply patches for severe, publicly known vulnerabilities but we do not update the various components automatically because this will often break a customer’s site or web application. We provide services for upgrades and migrations upon request for a billable fee.
3. There is no universal definition of PCI compliance. Various scanning services are used to certify PCI compliance and their exception reports are not uniform. We provide assistance as a billable service to interpret scanning reports, perform updates as needed, and interact with the PCI scanning service. PCI compliance assistance services are available on a billable as request basis and on a quarterly fixed fee basis.
As a managed service provider, we are constantly investing in innovative solutions to strengthen your security and ensure IT infrastructure sustainability. But we also believe in the shared responsibility model, where customers must also be part of the process. By understanding the shared responsibility model, we can ensure the security of your cloud infrastructure and improve your overall security posture.
 Broadwing Capital Acquires CloudScale365...
Broadwing Capital Acquires CloudScale365... 


