Spotlight on Sales: Meet New VP Evan Brown
Q&A Series with CloudScale365 Leadership CloudScale365 is entering an exciting new chapter of growth, and strong leadership is key to driving that momentum. In our latest Q&A series, we sat down with Evan Brown, CloudScale365’s new Vice President of Sales....
Microsoft 365 Support and Managed IT Solutions
Simplifying Business Technology for SMBs Microsoft 365 support and managed IT services play a critical role in helping businesses across the United States manage modern workplace technology efficiently. As organizations increasingly rely on cloud-based tools for communication, collaboration, and data...
Broadwing Capital Acquires CloudScale365
The acquisition marks a meaningful milestone for CloudScale365—one that is designed to bring even greater service, value, and innovation to managed IT clients.
Auditing & ComplianceCloud and InfrastructureCo-Managed ITFinancialFully Managed ITHealthcareManaged IT Services
Advanced Load Balancer Solutions
Discover how advanced load balancer solutions enhance IT infrastructure across various industries, including the financial and healthcare sectors.
Craft a Comprehensive DDoS Protection Strategy
Learn the important components for creating a comprehensive DDoS protection strategy to ensure uptime and security for your organization.
CloudScale365 Partners with Krista Software to Unlock AI-Driven Efficiencies for Internal Operations
Krista orchestrates people, applications, and agentic AI to automate entire business processes using natural language.
Cloud and InfrastructureGovernment and MunicipalitiesManaged IT ServicesMicrosoftNewsNon ProfitSecurity
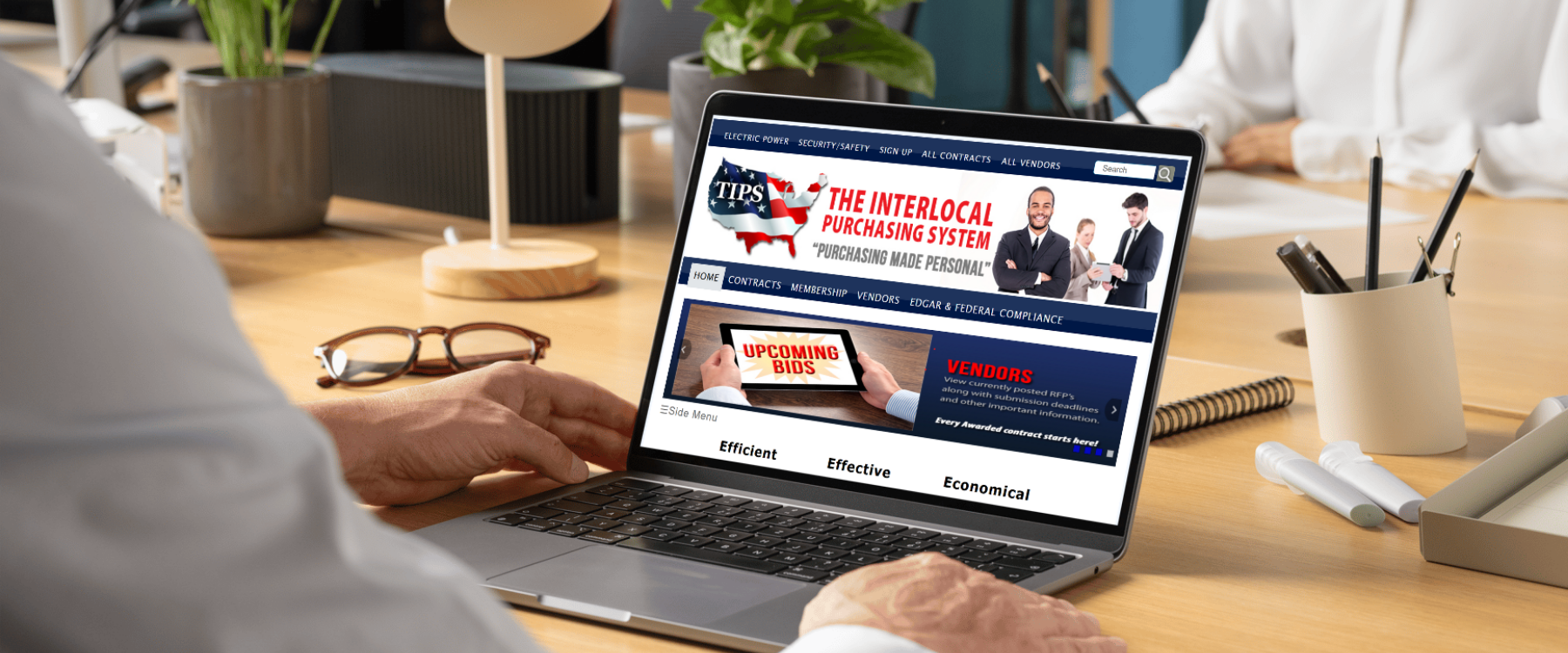
CloudScale365 Secures Ability to Bid Through The Interlocal Purchasing System (TIPS)
Government agencies, municipalities, schools, and non-profits gain access to competitive CloudScale365 pricing for IT services, while simplifying procurement and ensuring regulatory compliance.
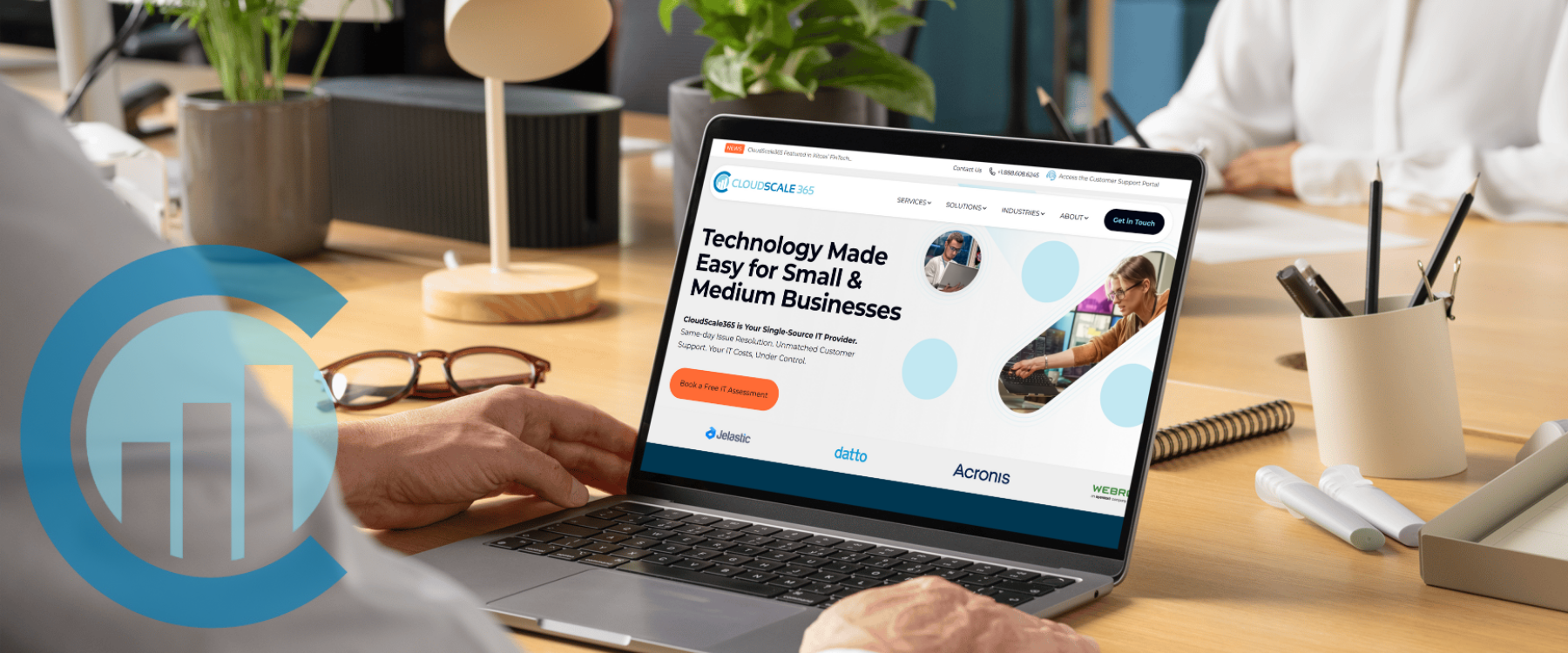
Welcome to the New CloudScale365 Website
Today, we’re thrilled to unveil the new CloudScale365 website: faster, clearer, and more aligned with the needs of modern SMBs.
Safeguard Your SMB: Why Endpoint Protection is Key
As small and mid-sized businesses increasingly rely on digital devices to operate, protecting those devices from cybersecurity threats has become a top priority. Endpoint security is crucial in safeguarding your organization’s sensitive data and network. In this blog, we’ll dive...
Unlock Performance with Enterprise Java Hosting for Business
For businesses and organizations looking to scale their operations, enterprise java hosting provides the reliability and performance needed for mission-critical applications. Java hosting offers unparalleled flexibility and robustness, whether you’re running a website, an online platform, or a web service....
 Broadwing Capital Acquires CloudScale365...
Broadwing Capital Acquires CloudScale365...