Fully Managed IT Services for SMBs: A Deep Dive
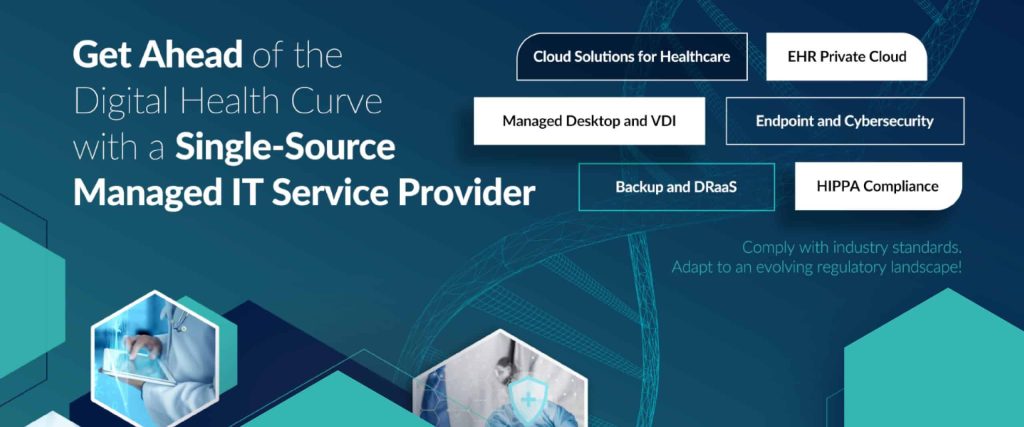
Understanding Fully Managed IT Services for SMBs: What are the Benefits—and Why It Matters Technology plays a critical role in how modern businesses operate, compete, and grow. From cloud platforms and cybersecurity to remote work tools and compliance requirements, IT
 Broadwing Capital Acquires CloudScale365...
Broadwing Capital Acquires CloudScale365...